Cyber Security Visuals Challenge
Part of Cyber Security Visuals Challenge.
I was among the TOP 25 DESIGNERS for CYBERSECURITY VISUALS CHALLENGE organised by OpenIDEO and Hewlett Foundation in 2019.
My submission centered around creating a set of interactive illustrations to simplify the concept of cybersecurity for the common public. The contest saw participants from 17 countries.
The problem statement:
How might we reimagine a more compelling and relatable visual language for cybersecurity?
I participated in the challenge to be able to make an effective system of illustrations and interactions, that can effortlessly create an persistent understanding of the topic.
Learnings from the sketching process
Much of the field of Cyber-Security is built on abstract concepts. Explaining these would require a deep understanding, hence I had to read about the common perspective that the general populace has.
I started with my parents to explore their understanding. Then I forwarded the same to some of my computing-teetotaler friends. I had to make adjustments, to bring out more meaning. Though the illustration still remains biased towards my understanding of the problem.
The World Wide Web is a dynamic medium. I have tried to respect the same here, by making all of my visuals interactive. The five ideas that I have tried to visualize are in increasing order of complexity, meaning C0 is easier to understand and discuss and C4 is the most complex requiring technical and social expertise, increasing in difficulty to comprehend in an progressive manner.
Target Audience: Anyone wishing to dabble in the intricacies of Cybersecurity.
My submissions:
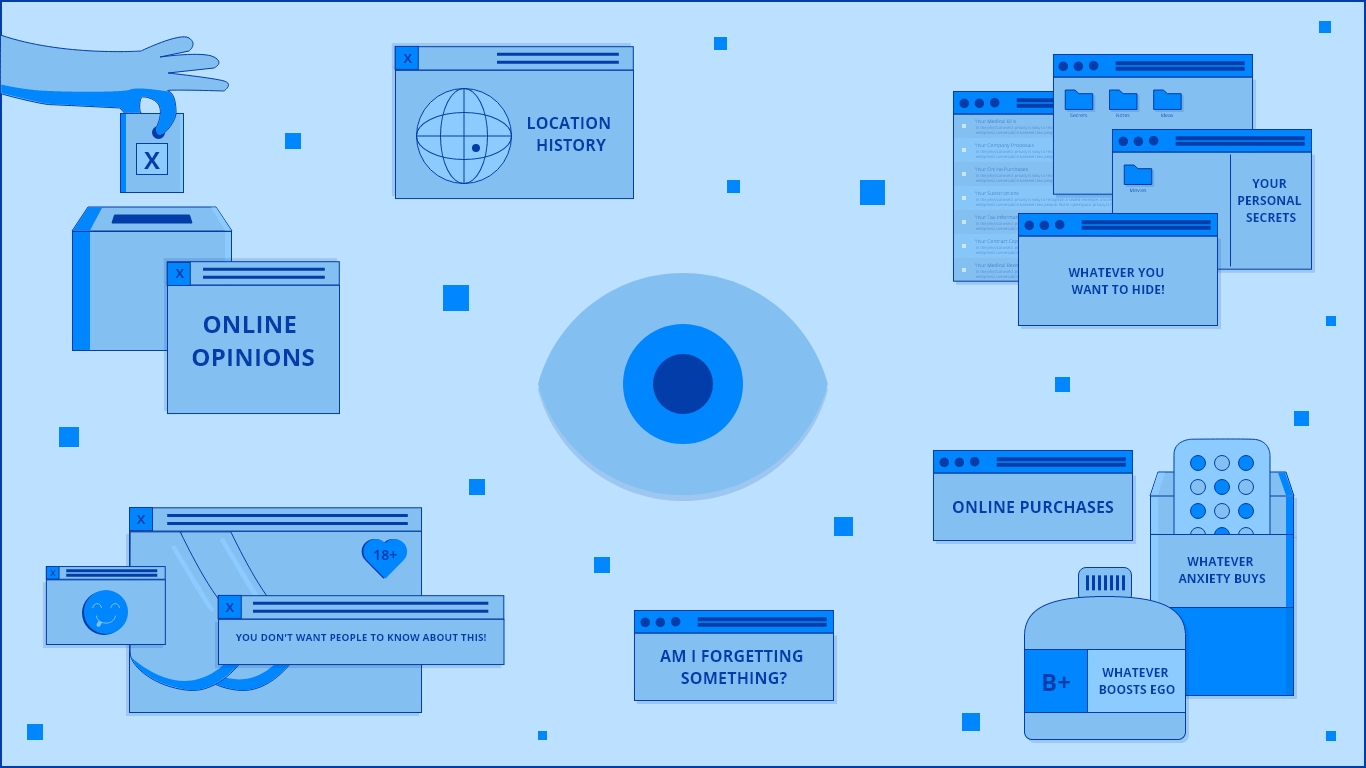
C0: The portrait represents everything that everyone knows and should know. An open secret, that we come across frequently. The portrait represents us, which subsequently opens up revealing deeper layers, that have been locked away. An exercise in iterative storytelling.
C1: Building up on my earlier submission, there are more layers now. More depth to the information that makes up our digital identity. Some surface level secrets and some deeper secrets. We, as humans are an incomplete puzzle trying to solve ourselves our entire lives.
C2: Building up on C1, here the data is collected and sent for compilation to create psuedo-personalities. An incomplete low-definition meaning of our glorious full lives. (Check the codepen at 0.5x zoom for the whole picture)
C3: We have increasingly began depending on black-box machine learning models for our every problem. But how unbiased are there results? Can they be influenced? I have tried to illustrate that here.
C4: Is disinformation a cybersecurity threat? If yes, how does it impact us in our daily average lives
These interactive visualization offer hands-on-learning, hence it could be useful in roping in passive learners and eventually enabling them to take an active interest. Examples: Cybersecurity Courses, Policy Campaigning, Explainer Editorials
What was the most useful feedback that you received?
The idea for Chapter 3 directly came out of the video conference I had with Steven Weber, my assigned mentor, where we discussed the reality of machine learning models and how could be they be represented. The idea for Chapter 4 came out of my discussion with a certain individual about network topology visualization and Yishi Deng’s entry on Divided truth. Robyn Hwang’s, (a participant) suggestion on Chapter 1 on segregating information into layers and revealing them progressively helped me add more depth. The questions that are part of Chapter 0 are a direct result of Jen Zariat’s entry on What is end-to-end encryption.
How do your concepts expand the conversation on cybersecurity? Each visualization is designed to offer insights, which can evolve into a personal perspective by the added interaction of a person. I have tried to make the level of open ended dialog and discussion on each visual in an increasing order of ascension. The people in the illustration are abstract vectors, made of circles and rectangles and my attempt has been to make them gender-neutral. I have drawn in wide varieties of analogies to anchor my ideas.
A portrait sliding to reveal its inner contents that question us to unlock them, a metaphorical magnifying glass to gaze into information abyss that people are, a curious eye in our monitor and the wheel of fortune that decides our faith, are all perhaps timeless in nature. Cybersecurity is an evolving topic, but the fundamental kernel remains consistent, i.e. the people that make and manipulate them. I have tried to illustrate this side of the story.
How have you been able to incorporate technical accuracy into your concepts?
I started by consuming a lot of cybersecurity topics that interested me. (Even Google recommended some). I got a broad idea of what I wanted to represent, after seeing other participant’s ideas, feedback and discussions. So I zeroed in onto specific cybersecurity queries to anchor my visuals. In the Wheel of Fortune idea, I had realised the way I could visualize a machine learning algorithm, but how to show that it can be manipulated ?
I searched and came upon an article explaining 4 basic ways of manipulating data. I tackled each one individually, and translated it to an intuitive interaction. Poisoning became using a slider to upload data onto the model, inversion became an extract button and passing the info to Poisoning window. Evasion meant changing a slight value to alter results and data impersonation became swapping portraits to mean two similar but very different personas.
